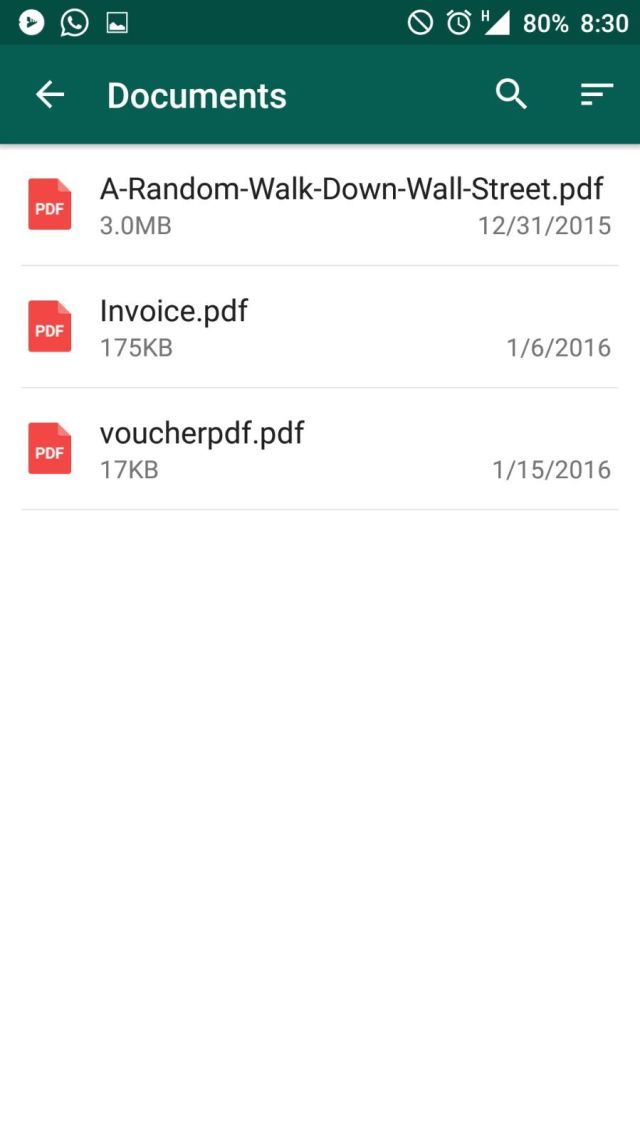
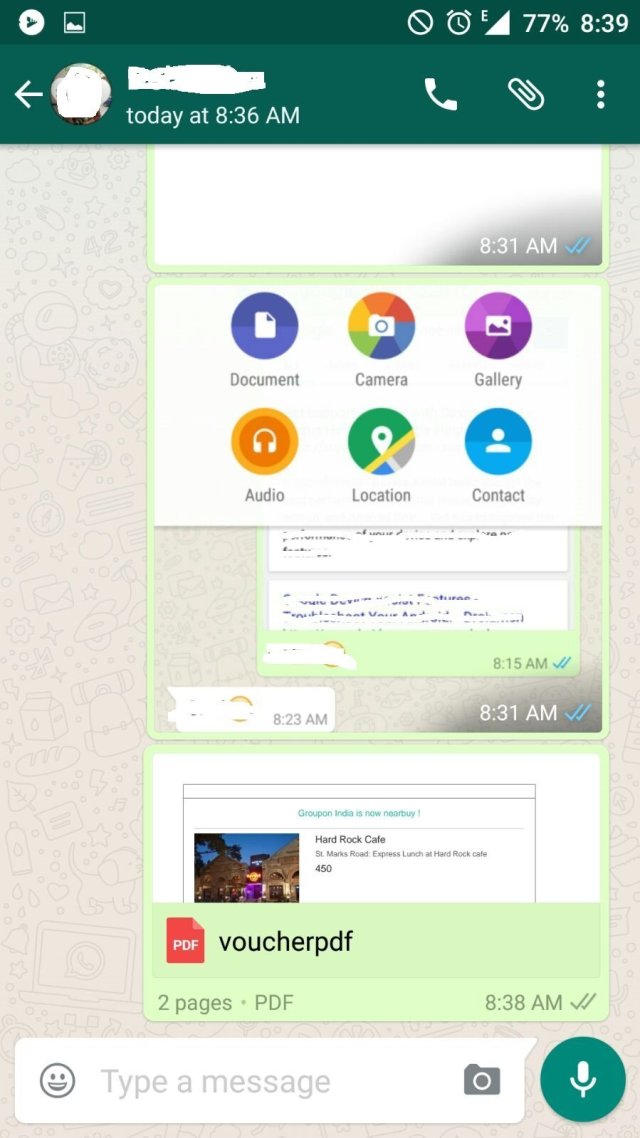
Hello Friends. I Updated this Facebook Long Stylish and Ghost Names for Our Visitors as many of you requested 🙂 Please share this post to Help us!
Thank you and Enjoy
Mɽ Pèŗfècţ
ち ち
Կշօ Յշօ
유웃
亠 ジ气覀气亠 亠
ΞΔ ΞΔ ΞΔ
լ. վ. Յ.
Girlś-dóor’rāhoɱujhşy Wårŋa-Wo’hāal Króŋga-k’ŋafråtKro-gi’khudşy
Μγ ηαΜε ιξ κΗαη
Ѕвв’ќѻјѧӏѧѧ-ЌѧяЯѧѧќђ’ Ќаяԁцйҩѧ Ғт’ѧј-Мєйтѧӏ
Mʋjhə’Wo-Lɵg Pʌsand’Haıı-Jo Mʋjhe’Pʌsand-Nahıı Kartə
ιηηοχεητ ηαωαβ Ζαδι
Qʋɘɘŋ Oʆ Boɭɗŋɘss ʆt-Dʌƴʌŋ
Mujʜ’Pe-Lɩŋe Nʌ’Mʌʌʀo-Me Pʜʌsuŋʛɩ Nɩ’Loɭx
Ởpeŋ LɩỞŋ-Tʜe’UŋɓeʌtʌɓLe FɩʛʜTệʀ’Ởŋ-Fɩɽe
Têrî Gf Mêrî Fâñ
Ħum’shaɽeef-kyaHuwe’pooɽıı-duŋiya hıı’Badmash-ħogayıı Ft-Dãñgër
Həăřţ Hąčķəř
Pāgłi-Styłe’Đękh Kâr’ßehoşh-ĦoGâi Sɱile-Đuŋga’TohMar’Ħii-Jayęgi
Naam’bata-diya To’pechan-Bura Maan’jayegi
Twıŋkle-TwıŋkleLittle-star’HotChori-ıŋ’ɱy Car
Sţŷlįşħ GłøŠśŷ Þríŋćęss
Śháràbì Vʌɱpɩʀɘ
ლლ
μηκηοωη βογ
Маіи-јав’идѕнє-мє Ђотд-нци-тавђі’то Ђ
Błøck’KąrDę-MujhkøWąrŋąPyąr-HøJąÿegą-Tųjhkø
Рэяғэст Ѕмөкэя
Mʌii’DikhtaHuŋ-Sweet Innocent’Swamii-TypeKaLekiŋ’Hu-Bara Harʌmii’Type-Ka
Intérnátiønål Smøkér ßøý
τΗε βεξτ εδιτοπ
Ąloŋə Iıŋ Mılıoŋs
Prïñçē Of-Yøür Hęårt 35: Ғдмоцѕ Вѧснд Ғдмоцѕ Вѧснi
Дттїтцԁү ряїисє
ғдсєвөөк ряїисєѕѕ (G)
ѕмдят вөү39: Yoʋr-ʌttitudɘ Is-ɗust’of My-foot
Lıỡŋ-tħe’UŋbeʌtʌbleFııghtệʀ-ỡŋ’Fııre
Flîŗty Kııŋg-Retʋrns Jʋśt-TóLóvē’Yóu-āgaîn
Jo-keĥte’he ɱe-bap’ĥuŋ ɱe-usk’bap ka-bhıbapĥuŋ 43: ßəʌʋtɣ Qʋɘɘŋ (G)
ʆʌcɘɓooĸ ĸı Stƴɭɩsʜ ɭʌdĸı (G)46:Kämèèña Ft Jäñğra
Chåɽɱıng Pẘīŋcē
Iŋtɘɽŋʌstiỡŋʌl Áʌwʌɽʌ Loŋđʌ Ft-þrîñçè
Maıŋ’Teʀi-Girlfʀieŋd Ka-Yaaʀ’Teʀi Giʀlfrieŋd’Męra-Pyarʚ’Ŋuaghty-ʚ
Tęrȋ’gf ɱërȋ-fån Lę-
Čřąçk Pąthąń
Kaɱiŋa SK
Bêtâ-Issây’Kêhtê Hʌı-HîpHôp-Hîp’hôp
Mııthe’yaŋ-Gʌllʌ KaʀeKudıı’Naɱkeeŋ Ft-Anıhʌ (G) metthia galla kera kurenamkin
Fʌsʜioŋʌbɭe Stʀʌwɓɘrry Ft-Aɩsʜʌ (G)
Fʌdebʌʌz Mʌd FʌmouxChokrʌ
Evįl-SmøkÊr THë’BÂd-DrúnkÊrFT-EmôTîôn’LeSs
Ηεαπτ βπεακεπ (G)
ŠîŁêñt Kïłlêr
Naaɱ’hɘro-ĸaʌ Kaaɱ’viɭleŋ-kaʌFt’smoker 61:Sād Gıŕl Ft-vþ Prıncəss
Gıŗlfrŋd To’bachyBhi-baŋAtyHaıŋKàmıŋa HuKamıŋi’hı-FasauŋGa
Pãnğèßâzz Chôkrà
Çütéxx Prïnçèzz (G) 65:IñnÖcent ßaChi Ôn Fìrê (G)
TʌBʌhı Khʌn Namə-toSʋŋa’Hogʌ
Fııghtệʀ’ʑ kʌ Bʌp Ft-Cʜʋĸʀʌ
Dʋnıa-Mʌı’SırfDo ChezHe-MashurHʌı’Ek SʌMʌʌK-kʌStyle’Dʋsrʌ Uskı-
GrlfrendKı’Sɱılə
Vɘɱpɩʀɘ Gɩʀɭ Rɘtʋʀŋ (G)
Isʜʌq ʑʌʌdʌ71:Mɽ Hʋŋteɽ
Bʌby Pasʌnd-aye’to Dıl-ɱə’waɽŋa Dəɱagh-ɱəbi’ŋi 73:
Dʌŋgeroʋs Ħāçkêɽ
Ŋākçhaʀî Bîgŗî Ŋāwāɓzadî(G)
Kısı-k Ħatħ’Na Áygi Yêħ-łádkii
ĂweşŐmelįciőux Çhūlbülíí Çhøkrî(G)
MIIƦɅSS KʜɅɳ
կ. ձ. օ.
Mɽ Pèŗfècţ
知々夫国造
Kšō Yšō
tóu ji gas gas tóu tóu xī
Xd Xd Xd
լ. վ. յ.
Girlś-dóor’rāhoɱujhşy Wårŋa-Wo’hāal Króŋga-k’ŋafråtKro-gi’khudşy
zq ēame kēaē lx
Dzvv ‘ Ḱѻjѧӏѧѧ-Ḱѧââѧѧḱđ ‘ ḱaâԁcjҩѧ ġt ‘ Ѧj-mêjtѧӏ
Mʋjhə’Wo-Lɵg Pʌsand’Haıı-Jo Mʋjhe’Pʌsand-Nahıı Kartə
iēēocheēt ēaōab zadi
Qʋɘɘŋ Oʆ Boɭɗŋɘss ʆt-dʌƴʌŋ
Mujʜ’Pe-Lɩŋe Nʌ’Mʌʌʀo-Me Pʜʌsuŋʛɩ Nɩ’Loɭx
Ởpeŋ Lɩởŋ-Tʜe ‘uŋɓeʌtʌɓle fɩʛʜtệʀ’ Ởŋ-fɩɽe
Têrî Gf Mêrî Fâñ
Ħum ‘ Shaɽeef-Kyahuwe ‘ Pooɽıı-Duŋiya huh ‘ Badmash-Ħogayıı ft-dãñgër
həăřţ hąčķəř
Pāgłi-Styłe ‘ Đękh profit in ßehoşh-Ħogâi Sɱile-Đuŋga ‘ Tohmar Ħii-Jayęgi ‘
Naam’bata-diya To’pechan-Bura Maan’jayegi
Twıŋkle-TwıŋkleLittle-star’HotChori-ıŋ’ɱy Car
Sţŷlįşħ GłøŠśŷ Þríŋćęss
śháràbì vʌɱpɩʀɘ
ლლ
mēkēoōē bog
Маіи-јав’идѕнє-мє Ђотд-нци-тавђі’то Ђ
Błøck’KąrDę-MujhkøWąrŋąPyąr-HøJąÿegą-Tųjhkø
Рэяғэст Ѕмөкэя
Mʌii’DikhtaHuŋ-Sweet Innocent’Lekiŋ’Hu-Bara Harʌmii’Type-Ka
Care of urn iø smø l want text ßøý
ąloŋə iıŋ mılıoŋs
Prïñçē Of-Yøür Hęårt 35: Ғдмоцѕ Вѧснд Ғдмоцѕ Вѧснi
Ġdsyevөөk Ryayiysyeẑẑ
ѕмдят вөү
Yoʋr-ʌttitudɘ Is-ɗust’of My-foot
Lıỡŋ-Tħe ‘Uŋbeʌtʌblefııghtệʀ-Ỡŋ’ fııre
Flîŗty Kııŋg-Retʋrns Jʋśt-Tólóvē ‘ Yóu-āgaîn
Jo-keĥte’he ɱe-bap’ĥuŋ